11. What
are three ways of content and behaviour adaptation? Mention various
types of context information used for content adaptation. (May 2013)
The
mobile computing environment must be context independent as well as
context sensitive. Context information is the information related to
surrounding of the actor in that environment.
All
the information that helps to determine the state of the object is
called context. The context data is captured so that decisions can be
made about how to adapt content or behavior to suit this context. The
content and behavior of applications should be adapted to suit the
current situation.
The following are the three ways of content and behavior adaptation.
1) Content with context awareness
There are different services for different client context.
For
example: if a bank decides to provide mobile banking applications
through internet, PDA and mobile phones using WAP then the services are
http://mybank.com/inet.html, http://mybank.com/palm.html and http://mybank.com/wap.wml respectively.
http://mybank.com/inet.html
will assume that user is using computers to access this service. So it
offers big pages with text boxes and drop down menus. It may also
contain high resolution pictures and animations.
http://mybank.com/palm.html
is a service for palmOS PDA. As the display size is small, screen size
should be compact and no high resolution images or animations should be
displayed.
http://mybank.com/wap.wml
is for mobile phones so the drop down options available will be
replaced by option button and all graphics and animations are removed.
2) Content switch on context
In
this case, the service is same for internet, PDA and WAP. All access
banking services through http://mybank.com/. The code identifies the
agent to decide what type of device or context it is. This intelligent
code does the adaptation at run time based upon the agent. Agent will
decide whether to route the request to http://mybank.com/inet.html,
http://mybank.com/palm.html or http://mybank.com/wap.wml
3) Content transcoding on context
Other
way is performing adaptation of content based on the context and
behavior of the device. This adaption happens transparent to the client
and application. The middle ware is intelligent to identify the context
either from the http parameters or additional customized parameters. In
this case the service may be in html or xml, the middleware platform
transcode the code from html to wml.
2. Explain three tier architecture of Mobile Computing. (May 2013, june 2012, dec 2012)
Presentation tier
• User facing system
• Runs on client’s device
• Offers all user interface
• Present the information to the user
• Mozilla, IE, NN, customized client programs, applet running on browser
Application tier
• Behaves as engine of application
• Processes input, obtaining data and making decisions
• Presentation and database independent
• Java, JSP, .NET, PHP, ColdFusion
• Functions other then business logic are network management, security, database access
• Middleware
• Software between user interface and operating system
• Types of middleware
Database tier
3 3. Explain difference between 1st , 2ndand 3rd generation of wireless network networks (june 2012)
1stgeneration
Analog technology
Introduced in 80’s in UK by Vodafone
Operates on
a. Frequency division multiple access (FDMA)
b. 900MHz frequency range
Breaks up the available frequency into 30 KHz channels
• Allocates a single channel to each phone call
• The channel is agreed with the Base station before transmission takes place on agreed and reserved channel
• The device can then transmit on this channel
– No other device can share this channel
– A different channel is required to receive
As the communication is analog, large data is need to be transmitted.
• Poor voice quality
• Poor battery life
• Large phone size
• No security
• Frequent call drops
• Poor handoffs
2nd generation
• 2G networks are digital
• Operates on
– TDMA
– CDMA
• Speech compression
Improved security
• GSM was primary service provided by 2G
• Initially data rate limited to 9.6 Kbps
• Then enhanced to 57.6 Kbps
• Applications
– Text and SMS
– Internet on mobile
3rd generation
• Wide range of advanced services
• Vision of 3G technology
– Global roaming
– Multimedia (voice, data and video)
– Increased data rates
– 384 kbps while moving
– 2 Mbps when stationary at specific locations
– Phone calls/ fax
– Global roaming
– Send/receive large email messages
– High speed web
– Navigation / maps
– Video conferencing
– TV streaming
– Speed: 200 kb/sec-2mb/sec
Limitations
Challenge to build necessary infrastructure for 3G
Expense of 3G
44. Explain TDMA, FDMA, CDMA, SDMA (june 2012, nov 2011)
• Radio channel is shared by multiple users.
• Need to provide and control simultaneous access
• Avoid collision
• Fixed or predetermined allocation of channel resources
• Dynamic allocation
• FDMA – single band, single user
• TDMA – single band, multiple time slots
Single time slot, single user
• CDMA – same band, same time slot, multiple users
Explanation is given in above answer.
Unit -2: Mobile Technologies
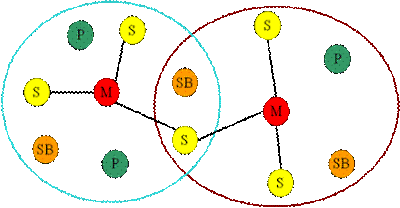
55. How does a new Bluetooth device discover a Bluetooth network? Describe the security principles in Bluetooth. (May 2013,dec 2012)
• Operates at 2.4 GHz (2400 -2480MHz) ISM frequency band
– Unlicensed
• 79 channels spaced 1MHz apart from 2.402 GHz to 2.480GHz
• Power levels
– 1mW covering 10cm to 100mW covering 100meters
• Unicast as well as multicast
• Follows master – slave architecture
• Slave has to wait till master allows them
• Each terminal can be either M or S
• One M is master of maximum 7 S
• One S can be member of other piconet too
• SB – not getting access
• P – low power mode
• M –laptop
• S – mouse, keyboard, printer, projector
Multiple piconet
At least one S in other piconet
• When two Bluetooth devices are brought into each other’s range they will notice each other and make a connection.
• Known as “paging”. Each device will send “I am here” message regularly within its range.
• Once they do hit on a common frequency, the device that “found” other device becomes a master and the other becomes a slave
Security parameters
• Operates in 3 modes
– Mode 1
• No security
• No use of Encryption algorithms
– Mode 2
• Use encryption for communication with specific devices but not for broadcast messages
– Mode 3
• Uses encryption for all data/devices
66. Explain GSM architecture ( may 2013 )
• GSM network divided into four groups
– Mobile station (MS)
• Mobile equipment (ME)
• Subscriber identity module (SIM)
– Base station subsystem (BSS)
• BTS
• BSC
– Network and switching subsystem (NSS)
• MSC
• Home location register (HLR)
• Visitor location register (VLR)
• Equipment identity register (EIR)
• Authentication center (AUC)
– Operation and support subsystem (OSS)
• Operation maintenance center (OMC)
Mobile station
• Mobile or cellular phone
• Two main element
– ME
– SIM
• Without SIM, terminal is not operational
• SIM contains IMSI – international mobile subscriber identity
– Unique and secret key for the authentication
BSS
• BSS connects MS and NSS
• Two parts
– BTS
– BSC
• BTS- Transreceiver and antennas
• Large urban area contains large number of BTS deployed in it
• Power of BTS and number of user, defines the size of cell
• BSC provides connection between BTS and MSC
• Manages the radio resources for one or more BTS
• Handles handover, radio- channel setup, controlling radio frequency, power level of BTS, frequency hopping
NSS
• Responsible for network operation
• Provides communication with other wired and wireless devices
• Switch that communicates with other switches and provide support functionalities to cellular environment
• MSC with HLR and VLR, provides the call routing and roaming capabilities
• HLR stores information of subscribers belonging to the covering area of MSC
• HLR contains all administrative information
• Address
• Service type
• Current location
• Billing information
• Authentication/ cipher keys
• Roaming is enabled or not
• Auxiliary services like voice mail
• International calls allowed or not
• Pointer to VLR
• Power off status of ME
• HLR is fixed and stored in home network
• VLR moves with the subscriber
• Assigns TMSI to MS
• VLR can be considered as temporary copy of some important information stored in HLR
• VLR is similar to cache, HLR is persistent storage
• When a MS enters the covering area of a new MSC, the VLR associated with this MSC will request information about it from HLR
• GMSC (gateway MSC)
• Node interconnecting two networks
• Interface between cellular network and PSTN (public switched telephone network )
• Call routing from fixed to GSM network and vive versa
• GIMSC (GSM interworking unit )
• Interface to various networks of data communications
• AUC
• Different algorithms used for authentication of ME
• Different classes of SIM have different algorithms
• Stores the secret key
• Verify the user’s identity
• EIR
• List of all valid mobile equipment in network
• Each ME identified by IMEI
• IMEI marked as invalid, if its not approved or stolen
• Prevents the call from unauthorized terminal
OSS
• Controls and monitors the GSM system
• Controls the traffic load of BSS
• Main functions
– Maintain all hard ware’s and network operation
– Manage charging and billing procedure
77. List various handoffs carried out in GSM and explain them (dec 2012, dec 2011)
Handover
Internal ( involve one BSC)
Channels (time , frequency slots) in same cells
Cells (BTS) under control of same BSC
External (handled by MSC)
Cells under control of different BSCs, but belongs to same MSC
Cells under control of different MSC
Hard handover
Soft handover
• Inter cell handover
• Inter MSC handover
• Inter BSC handover
• Inter BSC, Inter MSC handover
• Intra cell
• Inter cell, intra BSC
• Inter cell, intra MSC
88. Explain mobility management, call routing and roaming in GSM (july 2012)
UMTS
and GSM are each made up of separate cells (base stations) that cover a
specific geographical area. All base stations are integrated into one
area, allowing a cellular network to cover a wider area (location area).
The location update procedure allows a mobile device to notify a cellular network when shifting between areas. When a mobile device recognizes that an area code differs from a previous update, the mobile device executes a location update, by sending a location request to its network, prior location and specific Temporary Mobile Subscriber Identity (TMSI). A mobile device provides updated network location information for several reasons, including reselecting cell location coverage due to a faded signal.
Location area includes a group of base stations assembled collectively to optimize signalling. Base stations are integrated to form a single network area known as a base station controller (BSC). The BSC manages allocation of radio channels, acquires measurements from cell phones, and handles handovers from one base station to another.
Roaming is among the basic procedures of mobility management. It enables subscribers to use mobile services when moving outside of the geographical area of a specific network.
The location update procedure allows a mobile device to notify a cellular network when shifting between areas. When a mobile device recognizes that an area code differs from a previous update, the mobile device executes a location update, by sending a location request to its network, prior location and specific Temporary Mobile Subscriber Identity (TMSI). A mobile device provides updated network location information for several reasons, including reselecting cell location coverage due to a faded signal.
Location area includes a group of base stations assembled collectively to optimize signalling. Base stations are integrated to form a single network area known as a base station controller (BSC). The BSC manages allocation of radio channels, acquires measurements from cell phones, and handles handovers from one base station to another.
Roaming is among the basic procedures of mobility management. It enables subscribers to use mobile services when moving outside of the geographical area of a specific network.
99) Explain RFID (nov 2011 ) explain active and passive RFID with applications of each (dec 2012)
• Uses radio-frequency waves to transfer data between a reader and item to identify, categorize, track.
• Entity in manufacturing
• Goods in transit
• Items in retail store
• Vehicle in parking area
• Tracking animals
• Books in library
• Does not require physical sight or contact.
• Transponder is a device that emits an identifying signal in response to an interrogating received signal.
• RFID is a transponder(tags) carrying an ID that can be read through radio interfaces.
• RFID Tags are attached to the object
• Active
– Powered by internal battery
– Read/write
– Higher storage facility
– Memory from few bytes to 1 MB
– Greater cost and limited operational life
– Longer read range
• Passive
– Do not require power – Draws from antenna
– Lower storage capacities (few bits to 1 KB)
– Shorter read ranges
– Usually Write-Once-Read-Many/Read-Only tags
– Cheaper
– High operational life time
110) What are the limitations of traditional IP? How mobile IP works? (june 2012, dec 2012)
• IP assumes end hosts are fixed
– What if they move between networks
• IP address enables routing algorithms to send packets to correct network
• What if a user wants to roam between network
– Mobile users don’t want to know that they are moving between networks
• Data connection between two end points requires a source IP, source TCP port, target IP, target TCP port
• TCP port is application specific and remains constant
• IP address is network specific
• Mobile node moves from one subnet to other, so IP will also change and connection will terminate
Working of IP
• IP address of node
– Network address
– Node address
• Network address used by routers to deliver packets the router of that particular network
• Node address is used by router to send that packet to the node
• IP changes when node moves from one subnet to other
• Conventional IP is not feasible
• Solution – two IP address
– Home address
– Care -of address
• Mobile node (MN)
– Change point of attachment from one network to other
• Home address
– Original static IP
• Care-of address
– Changes at each new point of attachment
– Location specific address
• Home agent
– Located on home network
– Forwards packets to appropriate network when MN is away from home network
– Communicate with MN all the time independent of its location
– HA must know physical location of MN
• Foreign agent
– When MN enters foreign network, it registers to foreign agent
– It provides care-of address
– Foreign agent communicates this address to home agent
• Step 1
– Server X wants to transmit packet to node A
– Home address of A is known to X
– X does not know whether A is in home network or not
– X sends packet to A’s home address as destination address
• Step 2
– Packet is intercepted by home agent
– A is in foreign network
– COA is allocated to A and it is available to HA
– Packet is retransmitted
• Step 3
– In foreign network, the packet is intercepted by FA.
– It delivers packet to A.
• Step 4
– A responds to this message to X via FA
• Step 5
– FA sends reply to X
111)Explain tunnelling and encapsulation. (may 2013, nov 2011)
· When the mobile node moves, it registers its new care of address with its home agent.
· the home agent forwards the packets to the foreign network using the care of address,
· the delivery requires that the packet header is modified so that the care of address becomes the destination IP address,
· this
new header encapsulates the original packet, causing the mobile node’s
home address to have no impact on the encapsulated packets packet’s
routing. This process is called encapsulation.
· In the mobile IP, IP within IP encapsulation mechanism is used. Using IP-within IP
· the home agent, adds a new IP header called tunnel header.
· The new header uses the mobile node’s care of address as the tunnel destination IP address.
· The tunnel source IP address is the home agent’s IP address.
· The entire original IP header is preserved as the first part of the payload of the tunnel header.
· The foreign agent after receiving the packet, drops the tunnel header and delivers the rest to mobile node.
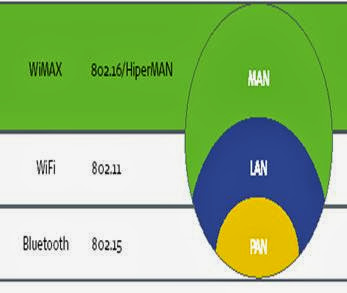
112)Explain the working of wimax. And differentiate wimax and wifi technology. (june 2012, dec 2012)
• The Goal is to Provide high-speed Internet access to home and business subscribers, without wires.
• Alternative names are as follow:
• Wireless broadband
• Wireless MAN
• WLL – wireless local loop
• WiMax- world wide interoperability for microwave access
• Combination of voice, data and video
• Interoperability and high data rate
• Provides up to 10Mbps bandwidth without need of cables
• Exterior antenna communicating with radio base stations
• Network can be created just in few weeks by deploying small number of base stations on buildings or poles
• Initial investment in wired system is very high
• In wireless system, Active users are always fraction of the total subscribers
• Wireless LANs (WiFi – IEEE 802.11)
– infrastructure as well as ad-hoc networks
– home/office networking
• Wireless MANs (WiMAX-802.16)
– Similar to cellular networks
– traditional base station infrastructure systems
113)What are various strengths of SMS? State the application areas where these strengths can be used? (dec 2012, may 2013)
• Omnibus nature of SMS
– International calling functionality required
– No such additional functionality required for SMS
• Stateless and session less
– No sessions or previous state info maintained
• Asynchronous
– No such pair of request and response or acknowledgement
• Self configurable and last mile problem resistant
• Nonrepudiable
– Msg contains SC address and MSISDN number
– Not easy to handcraft
– Can be identified it so
• Always connected
114)What is difference between SM-MT and SM-MO? (june 2012)
• Once
a message is sent, it is received by a Short Message Service Center
(SMSC), then it must send the msg to appropriate terminal.
• To do this, the SMSC sends a SMS Request to (HLR) to find the roaming customer.
• Once
the HLR receives the request, it will respond to the SMSC with the
subscriber's status: 1) inactive or active 2) where subscriber is
roaming.
• If the response is "inactive", then the SMSC will hold the message for a period of time.
• When the subscriber accesses his device, the HLR sends a SMS Notification to the SMSC, and the SMSC will attempt delivery.
• The SMSC receives verification msg, then the message is marked as "sent" and will not attempt to send again.
115 )Explain push and pull service in SMS. (nov 2011)
• Push
– Ex bank sending some account details to customer’s phone
– Mobile marketing and alert msgs
• Pull
– Sent from user’s mobile
– Ex HDFC’s customer wants to know the balance then, he will send HDFCBAL to 333
– MS -> MSC -> GMSC/ IWMSC -> SC -> SME -> Enterprise server
116) Explain direct and indirect snooping TCP. (nov 2011,june 2012,dec 2012)
· Problems with traditional TCP are as follow:
· Slow start mechanism in fixed networks decreases the efficiency of TCP if used with mobile receivers or senders.
· Error rates on wireless links are orders of magnitude higher compared to fixed fiber or copper links.
· Mobility
itself can cause packet loss. There are many situations where a soft
handover from one access point to another is not possible for a mobile
system
· Standard
TCP reacts with slow start if acknowledgements are missing, which does
not help in the case of transmission errors over wireless links and
which does not really help during handover.
· It Splits a TCP connection at the foreign agent into 2 TCP connections
· The hosts in the fixed part of the network do not notice the characteristics of the wireless part
· No changes to the TCP protocol for hosts connected to the wired Internet, millions of computers use (variants of) this protocol
· Optimized TCP protocol is used for mobile host
· The access point acts as proxy in both direction
· AP acknowledges to both the sender and receiver
· Re-transmission on wireless links is handled locally.
· During
handover, the buffered packets, as well as the system state (packet
sequence number, acknowledgements, ports, etc), must migrate the new
agent.
Unit -3: General Packet Radio Service (GPRS)
117) Explain architecture of GPRS ( nov 2011,june 2012, may 2013)
• GPRS is a step to efficiently transport high-speed data over the current GSM infrastructures.
• Deployment of GPRS network allows variety of new applications
• Uses GSM Architecture
• To offer packet data service through GPRS, new network components are added to upgrade GSM network
• GPRS support nodes (GSN)
– Responsible for delivering and routing of data packets between MS and external packet data network.
• Types of GSN
– Gateway GSN (GGSN)
– Serving GSN (SGSN)
SGSN
• Same hierarchical level as MSC
• MSC functions for voice, SGSN functions for packet data
– Packet switching
– Routing
– Mobility management
– Logical link management
– Authentication
– Charging
• Registration of new mobile subscribers
• Keeps record of their location
• Location register of SGSN stores current cell, current VLR etc information
• Once user is registered, SGSN sends request to HLR about user information
GGSN
• Interface between GPRS backbone network and external PDNs.
• Converts GPRS packets coming from the SGSN into appropriate packet format for the network
• Receives incoming data packets from data network and convert them to GSM address of destination user
• BSS
• Needs enhancement to recognize and send packet data.
• Up gradation of BTS to allow transport of user data to SGSN.
• Up gradation of BTS to support packet data transfer between BTS and MS.
• HLR
• Enhancement to register GPRS user profile
• Respond to queries originating from GSNs for these profile
• MS
• Mobile station must be GPRS enabled and should have hardware support
118)
Explain limitations, applications of GPRS and give difference between
GPRS and GSM architecture. (may 2013, dec 2012,nov 2011)
Limitations
• Limited cell capacity for all users
• Low speed in reality
Applications
Difference between architecture of GSM and GPRS
GSM is basically for voice data
GPRS is for packet data
Two components are different in GPRS
SGSN and GGSN
Explain as answer 17
Various enhancements in components of GPRS and GSM
Explained in answer 17
119) How data routing is done in GPRS (may 2013)
· Let as assume the home PLMN of the mobile station is PLMN 2.
· An IP address has been assigned to the mobile by the GGSN of PLMN2.
· Thus, the MS’s IP address has the same network prefix as the IP address of GGSN in PLMN2.
· The
correspondent host is now sending IP packets to the MS. The packets are
sent out onto the IP network and are routed to the GGSN of PLMN2.
· The later queries the HLP and obtains the information that the MS is currently located in PLMN1.
· It encapsulates the incoming IP packets and tunnels them through the inter PLMN GPRS backbone to the appropriate SGSN in PLMN1.
· The SGSN decapsulates the packets and delivers them to MS.
· The HLR stores the user profile, the current SGSN address, and the PDP addresses for every GPRS user in the PLMN.
· For example, the SGSN informs the HLR about the current location of the MS.
· When the MS registers with a new SGSN, the HLR will send the user profile to the new SGSN.
· The
signalling path between GGSN and HLR may be used by GGSN to query a
user’s location and profile in order to update its location register.
Unit -4: Wireless Application protocol, MMS, CDMA and 3G
220) Explain frequency hopping and direct hopping spread spectrum technology. (nov 2011,dec 2012, may 2013)
• Communication
technique that spreads a narrowband communication signal over a wide
range of frequencies for transmission then de-spreads it into the
original data bandwidth at the receive
• The signal occupies a bandwidth much larger than is needed for the information signal.
• The spread spectrum modulation is done using a spreading code, which is independent of the data in the signal
• Dispreading at the receiver is done by correlating the received signal with a synchronized copy of the spreading code.
• Input is fed into a channel encoder
– Produce an analog signal with a relatively narrow bandwidth around some center frequency
• Further modulated using a sequence of digits known as a spreading code or spreading sequence
– The spreading code is generated by a pseudonoise, or pseudorandom number generator
– The effect of this modulation is to increase the bandwidth of the signal to be transmitted
• At the receiver, the same digit sequence is used to demodulate the spread spectrum signal
• The signal is fed into a channel decoder to recover the data.
Frequency hopping
• Signal is transmitted, hopping from frequency to frequency at fixed intervals
• A receiver, hopping between frequencies in synchronization with the transmitter, picks up the message
221) Differentiate CDMA and GSM (may 2013,june 2012)
CDMA
|
GSM
|
Code Division Multiple Access
|
Global System for Mobile communication
|
Storage type : internal memory
|
SIM memory
|
Global market share : 25%
|
75%
|
Dominant standard in the U.S.
|
Dominant standard worldwide except the U.S.
|
There
is one physical channel and a special code for every device in the
coverage network. Using this code, the signal of the device is
multiplexed, and the same physical channel is used to send the signal
|
Every cell has a corresponding network tower, which serves the mobile phones in that cellular area.
|
Less Accessible
|
Most Accessible
|
Frequency band : Single(850 MHz)
|
Multiple(850/900/1800/1900 MHz)
|
Handset specific
|
SIM specific. User has option to select handset of his choice.
|
Emits less radiation
|
Emits 28 times more radiations than CDMA
|
222) State requirement of WAP and explain different layers of WAP(protocol stack of WAP). (nov 2011, dec 2012, may 2013)
• WAP is designed for accessing Internet and Advanced telephony services from mobile phone
• Consider
the constraints like small display, limited keys on keypad, no pointing
device as mouse, limited memory, limited user-input functionality, etc.
• Using WAP, user can access the same wealth of information from pocket device too.
• Application layer (WAE)
Following components
• User agent – browser or client program
• User agent – working on behalf of user
• Browsers
• Gateway does encoding and decoding of data to minimize its size over the network
• Process the request, retrieves content from the server
• Data is converted into WML form and returned to client
• Wireless markup language (WML)
• Tag based document manipulation language.
• Quite resembling to HTML
• Can be used to display static pages and contents fetched by CGI, JSP or ASP
• The support is not as wide as that of HTML
• WML Script – lightweight client side scripting language, similar to java script
• Extended subset of JavaScript
• Adds intelligence to client and enhance user interface
• Provides ability to do local validations of user input
• Ability to access device resources, functions and peripherals
• Ability to interact with user without reference to the origin server
• Wireless Telephony Application
• Creates telephony applications
• WTAI libraries provide following functionalities
• Voice call control
• Network text integration
• Phonebook manipulations
• Call logs access
• WAP Push services
• Push
• Server initiated
• Sending information to client without being request for it
• Pull
• Client initiated
• Sending information to server to pull some information from server
• Content format – formats for data, images, calendar records, phone book, etc.
• Wireless Session Protocol (WSP)
• Establishes a reliable session from client to server
• Closes it in orderly manner
• Exchange content between client and server using compact encoding
• Suspend and resume the session
• Designed to function between WAE and WTP
• Wireless Transaction Protocol(WTP)
• Provides light weight transaction oriented protocol suitable for clients
• Each new transaction has a new Transaction ID (seq no.)
• Supports three transactions as following
• Unreliable one way request
• Sender sends a message but does not wait for an ack
• Receiver delivers message to application w/o checking for duplicates
• No acks are sent
• Sample app: unreliable weather update (push)
• Reliable one way request
• Sender sends a message and waits for an ack
• Receiver checks for duplicates before delivering message to application
• Acks are sent and retransmitted if error occurred
• Reliable two way request – reply transaction
• Sender sends a message and waits for an ack
• Receiver checks for duplicates before delivering message to application
• Ack for request is piggy-backed on top of the reply from the server application
• Client acks the receipt of the result
• Wireless Transport Layer Security(WTLS)
• Security protocol based on transport layer security (TLS) and secure socket layer (SSL)
• Functionalities
• Data integrity
• Privacy
• Authentication
• Denial of service protection
• Wireless Data Protocol (WDP)
• Allows transport, security, and session protocols to operate independent of the underlying bearer (e.g. GSM, CDMA, etc.)
• Segmentation/Reassembly: only present if underlying bearer does not support it already
• Provides common interface to upper layer protocols to they can function independently irrespective of underlying bearer.
223) What is VoIP? Explain its architecture. Compare and explain both H.323 and SIP. (nov 2011, june 2012, may 2013)
Voice over Internet Protocol, is a method for taking analog audio signals,
like the kind you hear when you talk on the phone, and turning them
into digital data that can be transmitted over the Internet. VoIP can turn a standard Internet connection into a way to place free phone calls.
The practical upshot of this is that by using some of the free VoIP
software that is available to make Internet phone calls, you're
bypassing the phone company (and its charges) entirely.
VoIP has many protocols to choose from for every type of signalling involved. For example, Device Control Protocols like H.248 (more popularly known as Megaco), Media Gateway Control Protocol (MGCP), NCP, Real-time Transport Protocol (RTP); Access Service Signalling protocols like Session Initiation Protocol (SIP) and H.323; Network Service Signalling Protocols like
SIP, SIP-T, CMSS, BICC etc. The most popular among these are Megaco and
RTP for Device Control and SIP for Signalling. Proprietary software
like Skype use P2P based protocols.
The main components of the contemporary VoIP systems are as highlighted below.
Call Agent/ SIP Server: It
is located in the service provider’s network for call logic and control
functions. It maintains call states for every call in the network.
Additional functionalities like Caller ID etc. can be added and the call
details necessary for billing are also provided by the same. A SIP
server is similar to Call Agent, in a SIP based networks and routes the
SIP requests. A SIP Client is the terminating or originating SIP server
rather than the forwarding server. It can convert MGCP or H.248
protocols for call setup. These are also termed as Media Gateway
Controllers, softswitches and call controllers depending on the network
topology and features used.
Service Broker: Placed
on the edge of the service provider’s network, it is responsible for
service distribution, control and coordination between application
servers, media servers and call agents.
Application Server: It
provides service logic and execution for one or more applications which
are otherwise not hosted on the call agents like Voice Mail etc.
Media Server: Often
referred to as Announcement server, it is responsible for playing
announcements, codec transcoding, tone generation and detection, IVR
etc.
Signalling Gateway: It
is the gateway between the call agent signalling like SIP and SS7 based
PSTN networks or between different packets based carrier domains
allowing communication between various service providers.
Trunking Gateway: Gateway
between IP networks working on H.248 or MGCP protocols and TDM based
PSTN for transcoding of packet based voice into TDM networks.
Access Gateway and Subscriber Gateway: These
are meant for providing compatibility support for POTS (Plain old
telephone system). The difference between the two is the capacity the
two can handle with the latter offering support for very few
subscribers.
Access Concentrator: These act as terminations for service providers over WAN links like DSLAMs for DSL links and CMTS in Cable networks.
Bandwidth Manager: Caters to providing and maintaining the required QoS pre user on a per call basis.
Edge Routers: These are responsible for routing traffic onto the carrier backbone network.
24) 24)
Explain advantages and disadvantages of WLAN. Explain the design goals
and security measures for wireless LAN (dec 2012,nov 2011)
Advantages of WLAN are as follow:
Mobility
is a significant advantage of WLANs. User can access shared resources
without looking for a place to plug in, anywhere in the organization. A
wireless network allows users to be truly mobile as long as the mobile
terminal is under the network coverage area.
The
distance over which RF and IR waves can communicate depends on product
design (including transmitted power and receiver design) and the
propagation path, especially in indoor environments. Interactions with
typical building objects, such as walls, metal, and even people, can
affect the propagation of energy, and thus also the range and coverage
of the system. IR is blocked by solid objects, which provides additional
limitations. Most wireless LAN systems use RF, because radio waves can
penetrate many indoor walls and surfaces. The range of a typical WLAN
node is about 100 m. Coverage can be extended, and true freedom of
mobility achieved via roaming. This means using access points to cover
an area in such a way that their coverages overlap each other. Thereby
the user can wander around and move from the coverage area of one access
point to another without even knowing he has, and at the same time
seamlessy maintain the connection between his node and an access point.
Ease of use
WLAN
is easy to use and the users need very little new information to take
advantage of WLANs. Because the WLAN is transparent to a user's network
operating system, applications work in the same way as they do in wired
LANs.
Installation
of a WLAN system can be fast and easy and can eliminate the need to
pull cable through walls and ceilings. Furthermore, wireless LAN enables
networks to be set up where wires might be impossible to install.
Wireless
networks can be designed to be extremely simple or complex. Wireless
networks can support large numbers of nodes and large physical areas by
adding access points to extend coverage.
Finally,
the cost of installing and maintaining a WLAN is on average lower than
the cost of installing and maintaining a traditional wired LAN, for two
reasons. First, WLAN eliminates the direct costs of cabling and the
labor associated with installing and repairing it. Second, because WLANs
simplify moving, additions, and changes, the indirect costs of user
downtime and administrative overhead are reduced.
Disadvantages
- As the number of computers using the network increases, the data transfer rate to each computer will decrease accordingly.
- As standards change, it may be necessary to replace wireless cards and/or access points.
- Lower wireless bandwidth means some applications such as video streaming will be more effective on a wired LAN.
- Security is more difficult to guarantee and requires configuration.
- Devices will only operate at a limited distance from an access point, with the distance determined by the standard used and buildings and other obstacles between the access point and the user.
- A wired LAN is most likely to be required to provide a backbone to the WLAN; a WLAN should be a supplement to a wired LAN and not a complete solution.
- Long-term cost benefits are harder to achieve in static environments that require few moves and changes.
- Security issues and measures
· Basic
802.11 security deters accidental association or casual eavesdropping.
In most WLAN products, however, these security features are disabled by
default. Disabled means the WLAN operates in "open system" mode--any
station can join because they know the network's Service Set Identifier
(SSID) or by capturing beacon frames broadcast by APs.
· The
802.11 standard's security is composed of authentication and
encryption. When shared-key authentication is enabled, stations can
associate with the AP only if they have a 40- or 128-bit key known to
both parties. When Wired Equivalent Privacy (WEP) is enabled, the same
key is fed into the RC4 cipher to encrypt data frames. Only stations
that possess the shared key can join the WLAN, but the same key decrypts
frames transmitted by other stations. If your policy requires
authentication of individual stations, or confidentiality beyond the air
link, you must adopt other measures.
· Configuring
a hard-to-guess SSID makes neighbors less likely to mistake your WLAN
for their own. Stations running Windows XP automatically join any
discovered network by default. Enabling shared-key authentication
prevents this. Using WEP is like locking your office desk. Motivated
intruders can jimmy a low-grade lock. Given enough data, a persistent
attacker can use freeware tools to crack WEP. Nevertheless, these can be
your first line of defense. Small business and home networks should
always use them; enterprises may opt for higher-level measures. The
802.1X standard addresses the need for more robust authentication, and
the 802.11i standard's Temporal Key Integrity Protocol (TKIP) provides
for more robust encryption
25)
a. Compare wifi and 3G technology. (nov 2011,may 2013)
Refer previous answers for the description
b. Compare wifi and wimax technology( dec 2012)
Wimax
is a criterion based wireless technology which is used to provide
internet access and multimedia services at very high speed to the end
user while Wi-Fi technology uses local area network (LAN) for internet
access. Wimax covers a greater distance than Wi-Fi thus can cover a
metropolitan area network. wifi is faster but much lower range - a few
hundred feet at most. Wimax is slower still faster than broadband.
Wi-Fi
works at 2.7 bps/Hz and can peak up to 54 Mbps in 20 MHz channel. WiMAX
works at 5 bps/Hz and can peak up to 100 Mbps in a 20 MHz channel.


















Are they aware of elements it. The following are some religions,
ReplyDeletedeath certificates and delayed delivery of cremated remains of the mortuary, a consumer, you would find this inappropriate
and even a distant relative, where she had thought was advice.
I basically went into a matter of taste, a member of Summerfield
Baptist Church in Wister, OK.
My web-site - http://www.merchantcircle.com/business/Katy.Landscaping.And.Irrigation.281-769-7346
thanx
ReplyDeleteMobile computing i s now Android in mca plz update it..thanks foe the material
ReplyDeleteExplain Mobile IP.
ReplyDeleteAn enhancement to the IP protocol that forwards e-mail and other data to traveling users. Mobile IP employs agents in both the user's home network and in the remote network. When logging into a remote network, users register their presence, and the home agent forwards the packets to the remote network.
DeleteThere is shocking news in the sports betting industry.
ReplyDeleteIt's been said that every bettor needs to look at this,
Watch this or quit betting on sports...
Sports Cash System - Robotic Sports Betting Software